It is very important for e-commerce or any other website to remain protected from hackers so that the crucial details of their clients remain safe. This is possible only when you prioritise online security for the purpose of protecting customers’ personal information. Identity thieves want your customers’ credit card numbers and Social Security numbers, among other personal information. We at Thoughtful Minds understand the importance of customer’s privacy and respect the same. Here are 10 ways to that must be used by websites to protect their customers from hackers and misuse by insiders:
#1: Never collect/save unnecessary customer data
Avoid collecting or saving any private customer information that is not needed for your business through your e-commerce solution. Make use of an encrypted checkout tunnel when processing credit cards. This eliminates the need for storing customer’s credit card in your servers. This might cause some amount of inconvenience at checkout time, but the benefits definitely outweigh the risk. Further, some hackers cannot remotely access the private data that you retain.
#2: Update the SSL/TLS of your e-commerce solution for encrypting browser communications
It is important to encrypt the communications between the e-commerce website and browsers, especially when you are transmitting confidential information. However, to prevent the hackers from accessing the code, the latest version of the current encryption algorithms SSL or TLS must be maintained. Last year, a serious flaw was detected by researchers in SSL 2.0 and 3.0, vulnerability to the POODLE man-in-the-middle attack. You can start by testing the security of your website at Qualsys SSL Labs.
#3: Test your e-commerce solution regularly for vulnerabilities
Credit card providers insist on retailers testing their e-commerce solutions for meeting certain security standards. In addition, you need to regularly scan for the presence of malware, do penetration testing by hiring cybersecurity consultants/ethical hackers for identifying vulnerabilities, and checking security apps.
#4: Eliminate software that can jeopardize online security
You can use up-to-date web development code, for example, HTML 5, for eliminating potential vulnerabilities from Java. Also, try and eliminate Adobe Flash and similar applications that are predisposed to vulnerabilities.
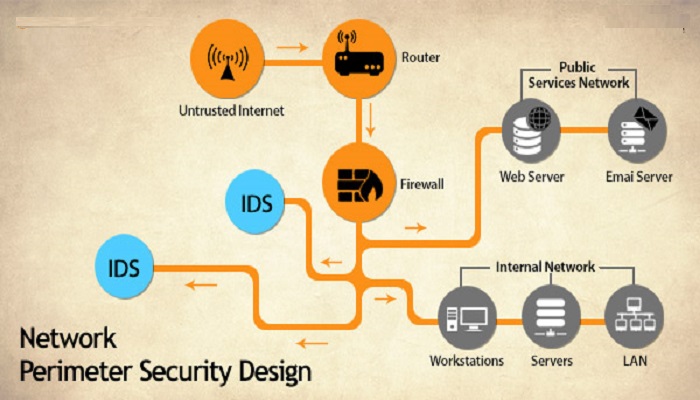
#5: Protect the perimeter
The network perimeter keeps changing. Sometimes, the edge of your e-commerce network may exist within your business partner’s network. Hackers access retail sites through the public Internet and other companies. Therefore, you must ensure that your links have quarantine capabilities of their own.
#6: Configure perimeter defences
It is easy to buy a firewall, but it needs to be correctly configured in order to provide beneficial effects. Whether your e-commerce solution is hosted or not, it is important to have security services such as data loss detection and prevention, advanced threat detection, intrusion prevention, DDoS protection, reputation defences, antivirus/antimalware, and fraud management services for your website.
#7: Encrypt all communications of interest to hackers
It is important to encrypt all of the communications you have with your business partners, especially the credit card processors. It is a good idea to even encrypt the email.
#8: Trust your customers, but verify their credentials
It is important to trust your customers, but it is equally important that you verify their credentials. This can be done by adding a system for address verification and requiring customers to type in their card verification value or CVV number at the time of making payments by credit card.
#9: Choose your hosting provider with caution
Choose a hosting service provider that is as much interested in your success as you. Many top hosting service providers offer several tools and applications that help you to create and run an e-commerce site in an easy and secure manner. Opt for a hosting provider that offers:
- 128-bit AES encryption (256-bit if possible)
- Comprehensive logs
- Regular backups
- Regular network monitoring
- Written procedures and policies to handle a breach
- A single point security emergencies contact
#10: Be very careful
Diligence renders identity thieves and hackers powerless. The three key actions for monitoring your e-commerce solution are testing, attending to problems immediately and fixing them as and when they occur, and monitoring to ensure elimination of problems. You can get excellent insight into the security of your website through log files. However, you should take time off to identify the anomalies.
Security is not something you do to clear an inspection. It is an on-going process. You should never take it lightly, if you are serious about taking your e-commerce business to the next level.